Should you cover your webcam?
The rapid growth of remote and home-working has led to manya lot of users getting webcams or setting up Zoom equipment in their own homes, and in many cases, often in rooms or parts of the house where there wasn’t previously a computer.
In 2016 Mark Zuckerberg inadvertently brought attention to the risks of users being covertly monitored through their computer’s webcams or mics when he posted a now-infamous photo of his desk setup, showing his laptop with a covered webcam and blocked mic. If even the creator of Facebook blocks his, who else does? Many people, it turned out, including former FBI director James Comey.
The risks, revisited...
Plenty has changed since then both in terms of improvements to security, but also in terms of risks, and we’re going to take a short look at the best practise to stay secure with your computer’s webcam and mic. The fears people talked about in the past, of ending up beholden to remote blackmailers are much less likely than problems closer to home, such as spousal stalkerware.
A host of these products have sprung up over recent years, and increasingly manage to sneak into otherwise safe environments. EpocCam is listed on both Apple’s App Store and the Google Play Store, bills itself as “a perfect baby monitor, spy-cam, security camera and pet-cam”:

Even seemingly reputable news sources fall prey to this, with Apple News running content from Pocketlint, explicitly geared around illegal remote monitoring. There is, sadly, a market for this sort of content and product.
That said, user privacy can be violated by simple accident, and without malicious intent. Plenty of Zoom users haven’t realised that their cameras were on, or that when joining a Zoom call that the call host might have configured the call to start with user cameras on. Additionally, it’s possible to join a Zoom call with one’s camera off, be placed in a waiting room before the call begins, and then have the camera turn on once the host admits the user to the call.
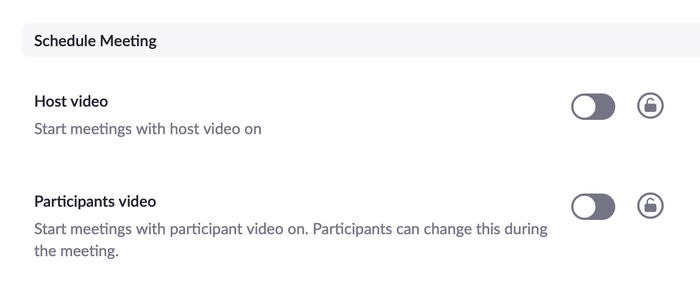
There are only a few video apps where the host can remotely enable video if the participant has turned it off after the start of the call, and Zoom is safe in this regard. It does, however, have a feature whereby the host can remotely unmute a participant’s microphone. If you’re in the habit of stepping away from your computer on long calls to get a cup of coffee whilst muted, beware that you might be unmuted without knowing about it. Similarly, if you’re joining the call from a room with other people around, their unexpected presence in your background may cause them embarrassment if they’re not expecting to be broadcast.
These inadvertent risks can be handled with a few simple precautions: covering or physically disconnecting a webcam makes things more obvious, and having a mic with a physical mute button helps. Before we get too deep into the answers, there are a few other things to think about.areas to delve into.
Securing your camera and mic on an iPhone
iPhone and iPad users have the least to worry about of all. So long as their device has not been jailbroken, it is extremely unlikely that hackers can remotely monitor the device’s camera or mic. Apple’s release of iOS 14 has done even more to safeguard users with its new orange and green dots.
Of course, it’s still possible for apps to access an iOS device’s camera and mic, but in order for this to happen, users must first install an app and grant it permission to record video and audio. It’s possible for apps to record audio -- but not video -- whilst backgrounded, but again, permissions must first be given by the user. Yes, there’s always the possibility of state-level cyber-espionage, but this is unlikely to affect the average user and is almost impossible to mitigate for, short of not using technology.
Broadly speaking, your iPhone and iPad should be perfectly safe so long as you don’t let them out of your sight, and only install apps that you trust.
Securing your webcam and mic on a Mac
A Mac, or a MacBook Pro is second only to an iPhone in its security. Recent Macs include something called a “T2 chip”, which includes a number of hardware-based security features. Most relevant of all, it uses hardware to physically disable a Mac laptop’s microphone when the laptop is closed or suspended.
From a practical perspective, it’s impossible for the Mac’s webcam to be in use without the accompanying green light being turned on. In the past, there have been workarounds for this but the known exploits have been fixed on Macs.
Still, software on the Mac does n’ot trigger any sort of system-level security prompt when accessing a webcam or mic, so users must be careful to only use apps they trust, and not to disable any system-level protection that is enabled on all Macs by default. AIt’s possible for any website that a user is visitingon canto request camera and microphone access, but the user’s browser -- Chrome, Safari, etc. -- will first prompt the user to give permission.
Security-conscious Mac users may wish to try OverSight (free) or Micro Snitch (paid), popular security tools that run in the background and alert users to any apps accessing their camera or mic.
Staying secure on Windows or Android
Unfortunately, Windows and Android users will have the hardest time of all staying secure. Often the software and hardware for these devices are made by different companies, meaning there’s plenty of room for loop-holes between the two. Google’s Play Store is infamous for including malware apps on a regular basis, and many Android phones (over 1bn!) suffer from not getting access to the latest security patches or Android updates.
Theoretically, modern Android devices with the latest security patches will be close to an iPhone’s security -- at least, each app must prompt for webcam or mic access, but a status light won’t be shown -- but the problem is it’s hard to tell by looking at an Android device if it’s secure or up to date. If yourSimply because your Android phone says it has all of the latest security patches, that doesn’t mean that the manufacturer of your Android phone has made all of the important security patches available. From this perspective, we’d be most likely to trust an Google Android device made by Google themselves (such as the Pixel), as Google makes both the software and hardware together, and are ultimately responsible for issuing the most important security updates.
Staying secure on these platforms is hard. The problem on Windows is so endemic that both Lenovo and HP have started building physical switches and covers into their webcams to give users some peace of mind. Alas, without hardware control of mic, it’s impossible to tell if a Windows laptop could be recording in the background when open or closed. Blocking microphones isn’t easy: you can’t cover them with a piece of tape like you can a camera, or at least if you do, it won’t be at all effective, as this video shows.
Most Windows devices will disable their internal microphone when an external mic is plugged in, and dedicated mic blockers exist for that purpose. However, it’s very hard to confirmtell whether your specific device really will fundamentally disable its internal microphone when this is done.
Our advice, if running Android, would be to only use Google devices such as the Pixel, and to avoid installing third-party apps from the Google Play Store. The risk of malware or app impersonation is not small. Seriously, if you want apps, use an iPhone. A month doesn’t pass without a news report of millions of Android users being infected by malware
What about Alexa or the HomePod?
Plenty of users have an Alexa or HomePod device in their home, or other forms of smart devices like thermostats or security cameras. These are all capable of broadcasting video or audio captured within the home. It’s very hard to keep tabs on these, and ultimately one must either trust the company making them or not. Both Amazon and Apple home devices may be listened to by staff in some circumstances, though there are controls that can enable users to opt in or out of parts of this.
If one has smart devices at home, it’s sensible to behave as if one’s audio is being recorded. That is potentially quite a burden. It’s very much not a good idea to buy smart devices from small, untrusted or unknown vendors. Who knows what their security is like?
Top tips to stay secure
Whilst there’s less for modern iPhone and Mac users to worry about, there are still a set of best practises we’d recommend for all users.
- Covering your webcam is important on a PC, but it’s arguably helpful for all users, in that it will serve as a reminder to think about security whilst using the computer. Realistically, you’re more likely to inadvertently broadcast yourself without knowing than you are to be remotely monitored by anyone else, and a cover helps make that risk obvious. Anything that makes you more security conscious is likely a good idea. You’ll see no end of ads online trying to sell plastic webcam covers: these are junk, and you don’t need them. A piece of tape or a sticky note is good enough for Mark Zuckerberg, and it’ll work well enough for you. Any residue left behind will be easy to remove. And besides, well-designed laptops won’t leave enough room to be closed without damaging themselves when an additional plastic cover is stuck on.
- Even better, use external, physically connected camera and audio devices. Relying on an external mic and cameras makes it crystal clear whether they are physically connected to your computer or not. This has the advantage that you can then permanently block your device’s internal camera and mic. Camo is a good example of a product like this, and has the additional benefit of greatly increasing the quality that a user will get when they join calls. Beware of products that require installation of drivers, or which are from unknown or untrusted sources.
- Close your laptop or power off your computer when not using it will make it harder or impossible for people to access it remotely.
- If you step away from your Zoom call whilst muted to make a coffee, beware that a host might remotely unmute you without you knowing. If your mic has a physical mute button you’ll be OK. But if you’re using AirPods, or an internal mic, there’s no mute that can override Zoom’s settings. If you’re on a call, always assume you might be overheard.
- Keep your software up to date, especially the main software on your phone and computer, and any browsers you use.
- Don’t disable your computer’s firewall or malware. Nowadays these are enabled by default on just about every type of computer and phone, and there’s little need to install additional software, beyond specific products for monitoring webcam use (see above).
- Be aware of your background. If other people might wander into shot, or you might have mess or private items around you, consider hiding your background whilst on calls.
- Be aware of general security best practises and be sure to securely store any video, audio or photos that you’ve already taken.
- Don’t let anyone untrusted use -- or repair -- any of your devices. Who knows what they might install or change in them.

